Expo
This edition the Expo will be themed “Let’s Collaborate – The Start-Up Edition”. A variety of organisations will showcase their collaborations here, including their success stories and learnings
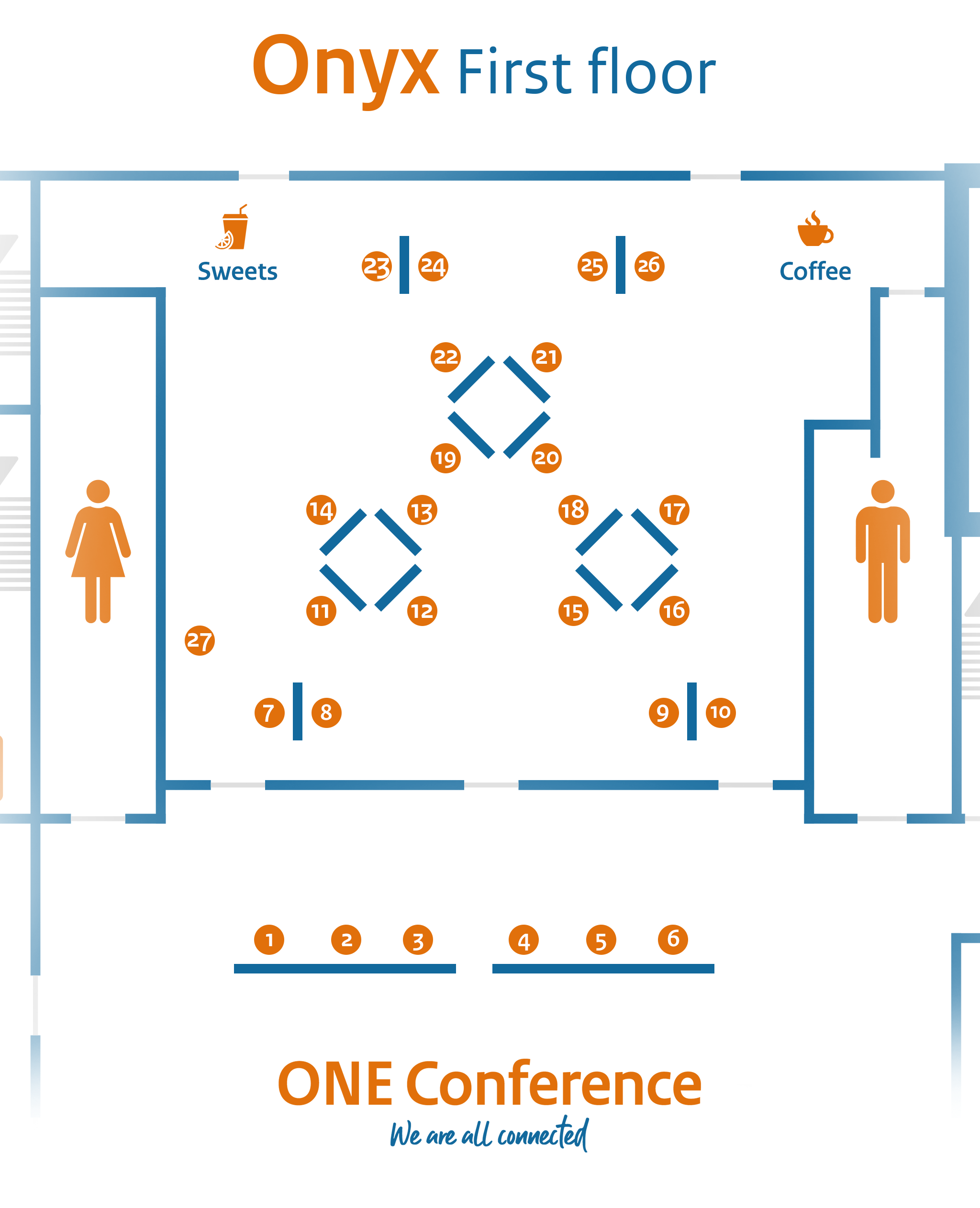
Exhibitors list (in order of booth number)
RiskApp is your “Strategy Guide for Application Risk.” RiskApp offers a comprehensive solution that starts with an AppSec/CMDB maturity assessment. We integrate with existing AppSec investments through robust APIs, transforming siloed information into actionable insights. This empowers organizations to act based on their risk appetite, tolerance, and acceptance, enabling CISOs to confidently embrace innovative applications while maintaining a strong security posture.
Headquartered in the Hague Security Delta, a premier cybersecurity hub, RiskApp is at the forefront of advancing application security and compliance. Since our inception in September 2023, our BETA product has launched successfully, and we are working with pilot customers across the Netherlands, the EU, and the USA. At the One Conference, we aim to demonstrate how RiskApp simplifies and enhances application risk management, helping enterprises fully leverage their existing AppSec investments. Discover how RiskApp can transform your approach to application security, fostering a secure, agile, and innovative business environment. Join us to see how we are shaping the future of application risk management and compliance.
What if Cyber Security Defenders could consistently outpace their adversaries? Become even faster, smarter, and have better predictive insight?
Practitioners are combating cyber attacks by increasingly sophisticated threat actors – and we have a way to help get ahead of these. Modat.io was created by researching, listening to, and directly experiencing the needs and challenges of security practitioners. Our products enable the community of defenders by giving contextualized data at scale, which leads to speed, ease, and relevancy.
Modat.io is the only European player with two value-based products that narrow the gap between defenders and adversaries: Modat Internet Search Index Solution (for defenders and security teams) and Modat On-Demand Scanning Services (for enterprise)
Modat will transform Security Teams’ offensive and defensive capabilities utilizing progressive technologies like advanced machine learning techniques. Now, hunters/researchers can uncover and track threats more effectively, reporting them before exploitation. Plus, with the changing compliance and regulation needs from the European Commission for 2025, we satisfy the Duty of Care in NIS2.
Our products assist individuals, companies, and governments who are increasing their cyber resiliency.
We are actively joining the fight to get ahead of cyber attacks by narrowing the growing gap between digital threats and resilience. Join us to outpace and outlast.
Chunk Works is proud to present its flagship product, QuSec®, at the ONE Conference. QuSec simplifies data security, makes it more secure, and reduces costs by combining multiple data security categories into a single platform. It protects your data from both current and emerging threats, such as ransomware, AI attacks, and advances in quantum computing, making your data future-ready.
Key features of QuSec:
– Crypto-agility enables quick replacement of compromised encryption algorithms.
– Hybrid encryption makes legacy devices future-ready without hardware upgrades and protects networks from compromised algorithms.
– Autonomous data recovery and decentralized routing ensure data integrity and availability, even under attack.
– Deployable on existing infrastructures and improves security without requiring hardware replacements or cloud migration.
– The innovative design improves data security, while reducing complexity and backup overhead, and, with that, is very cost-effective.
Founded in 2019, Chunk Works operates with the innovation ethos of Lockheed Martin’s Skunk Works. Its dedicated team of professionals drives rapid development to stay ahead of cybersecurity threats. At ONE Conference, they will showcase how QuSec’s features can revolutionize data security, providing robust protection against current and future cyber threats.
Masero BV is a young and innovative cybersecurity partner that assists companies in defending themselves against the growing threat of cybercrime. By offering insight into the current security status, Masero collaborates with organizations to develop an effective security strategy.
With the upcoming NIS2 regulations in sight, we help organizations to take the necessary operational and organizational measures. Among other things, NIS2 mentions chain responsibility, making organizations responsible not only for their own security but also for that of suppliers.
Masero has developed a way of working that makes it possible to protect SME’s against attacks at the same level as large enterprises are used to, but at a cost that is interesting for SME’s. To provide this, we have set up a Security Operations Center (C-SOC) where cybersecurity experts can respond to (potential) incidents in customer environments 24/7.
We have automated our methods in a way that we can quickly include the customer’s IT environment in our monitoring dashboard, start securing the environment and suggesting areas for improvement from day one. This way of working makes it possible to significantly increase and maintain the security level of both small and large enterprises.
Insiders do not suddenly emerge. People do not suddenly ‘snap’ and start engaging in acts of data theft or violence. The path towards insider acts is evolutionary, with signposts along the way. Thus, if you want to understand threats and predict who may conduct an insider act, then you need to understand the signs.
At Signpost Six, we have developed a holistic Insider Risk Assessment Framework, which is unique in the market. Our approach leverages our team’s deep expertise to identify and interpret these critical signposts, while focusing on employee loyalty and wellbeing. By understanding these indicators, we can support the public and private sectors with tailor-made insider risk assessments, programmes, and awareness solutions.
Signpost Six and Arda have come together to develop bespoke crisis simulations, equipping organisations with the tools they need to tackle security threats effectively. Our collaboration combines expertise in insider risk with Arda’s innovative approach to building continuous awareness programmes. Together, we offer an awareness solution to the growing security challenges facing organisations today.
Pentest Demand is Soaring, But Where Are the Pros?
We’ve all seen the headlines: cyberattacks are up a staggering 72% since 2021 (Forbes Advisor). The EU is tightening cybersecurity laws with the new NIS2 directive, pushing organizations to ramp up their security assessments. However, a massive shortage of cybersecurity experts is rapidly increasing, driving costs through the roof. Clearly, we need smarter, more efficient ways to handle security assessments.
Efficiency Boost: From Vulnerability Discovery to Mitigation
Meet Reporter – your security team’s new secret weapon! Reporter allows pentesters to focus on creating top-notch, industry-standard security reports instead of getting bogged down by repetitive tasks. Our collaboration tools supercharge efficiency and quality. Streamlined review flows ensure top-tier assurance, while retest flows make vulnerability mitigation a breeze. Template improvement flow means new findings are published faster. Communication tools enable pentesters to share critical info during assessments and keep stakeholders in the loop with updates.
Complete Control Over Your Data
As a Dutch company focused on the European market, we understand the importance of data privacy. Reporter is available exclusively as a flexible on-premise/self-hosted solution, built to comply with the world’s strongest data privacy laws. This commitment to security and flexibility is why top security firms and enterprises, including Europe’s largest banks, have chosen Reporter.
YES!Delft provides an environment where tech startups with promising ideas grow into successful companies. Do you have a clear business idea, an innovative technology and you wish to kickstart your business in an environment where innovators thrive? You’re welcome to join YES!Delft as a startup. Now with a clear cyber track in our next program, come by to ask for more information.
The hackers perspective
Defensive security should be validated by offensive security. Hadrian provides the hacker perspective, revealing the targets and methods that could be used in a real-world data breach. Hadrian’s continuous and comprehensive testing discovers and validates risks completely autonomously.
Hadrian’s platform combines attack surface discovery, automated penetration testing, and threat exposure management technologies in a cloud-based and agentless platform. The cutting-edge technology is constantly updated and improved by Hadrian’s in-house hacker team.
We are Upfront Security, a software company, specialized in providing actionable alerts for individuals with insights into the use of personal data in order to prevent and recognize identity fraud. Monitoring personal information is the best and most affordable early detection and deterrence systems for Identity Fraud.
With our own proprietary technology and platform, we are the first and only Identity Monitoring provider based on economic transactions with ID-documents. We raise awareness by providing low-threshold and user-friendly tools that help protect personal data.
Our clients are organizations that want to make our tools available for their clients or employees. Either in order to mitigate their own Identity Fraud risk or as a Value Added Service in order to create client engagement and/or fulfill their Social Responsibility ambitions.
Risqui is a risk management tool developed by information security professionals to support efficient and effective risk management. It automates much administration, provides accurate insights in the risk management progress and has thoroughly validated A.I. integration to provide tailored advice on risk treatment strategies. Risqui will make the life of a CISO significantly easier and increases the quality of the risk management process. All packed into an easy-to-use and visually appealing application. Of course, being developed by information security professionals, security is a top priority. With the help of the CIF-NL subsidy, Risqui’s security has been greatly improved.
Risqui is a Dutch company and spun-off from Pasquil, a boutique consulting firm for information security and privacy.
SnapAttack is a threat-informed decision engine that connects your tools, analyzes your data streams, and tells you which threats matter so you can proactively defend against them. The SnapAttack SaaS Platform enables threat hunting and detection engineering through collaboration around threat intelligence, attack emulation, and behavioral analytics. With the platform you can build, test, and validate detections automatically & continuously to ensure security coverage is sound against key threat vectors. This insightful approach helps organizations proactively identify potential vulnerabilities, risks, and gaps in their defensive posture before an incident occurs. SnapAttack’s seasoned experts deliver forward-leaning threat hunting, detection-as-code, and actionable intelligence in a single vendor-agnostic solution. SnapAttack was incubated in Booz Allen’s Dark Labs and is rooted in years of real experience in both nation-state and commercial cyber operations and tradecraft. In 2021, SnapAttack was established as an independent company focused on rapidly evolving its platform capabilities and has continued to grow internationally across a government and commercial customer base.
Visit Website: https://www.snapattack.com and https://cloud.google.com/security/mandiant for more information.
Attic for Microsoft 365
Affordable Hardening & Automated SOC-as-a-Service
Microsoft365 is the core of IT, but does it get the defensive attention it deserves?
Attic Security, created by Zolder’s ethical hackers, provides top-notch cybersecurity operations for Microsoft365. Attic offers simple tips and one-click fixes to address insecure configurations in Microsoft365 and empowers all great security features that are disabled by default. Optionally, Attic will enable the functionality of Microsoft Sentinel, providing an actual SOC function to cover incident handling like NIS2 demands. Attic findings can be managed from a web-based customer portal or a mobile app, allowing for rapid fixing of incidents anytime anyplace.
Attic is a fully automated SaaS. As a result, you can help yourself in onboarding your Microsoft365 tenant into our service within minutes. Attic can be acquired by individual organizations and by MSPs looking to integrate our hardening and monitoring into their own Microsoft365 offerings.
Finally, Attic offers a program for agencies such as FERM Rotterdam in which we create a customized version of Attic for Microsoft365 which is connected to the MISP Threat Intelligence server allowing for quick response in case of widespread attacks, covering even the smallest SMEs.
Try Attic for free: atticsecurity.com/try
Project APPtake is collaborationa supported by the European Cybersecurity Competence Centre (ECCC) and includes partners from Italy, Poland, Hungary, France, Greece and the Netherlands. The project aims to strengthen the uptake of innovative Application Cybersecurity Solutions and build a portfolio of sustainable application cybersecurity solutions to foster the adoption of DevSecOps practices by the European SMEs, increasing their cybersecurity.
The Ceeyu SaaS platform makes supply chain risk management easy as pie for companies subject to NIS2 or DORA. The platform periodically performs automated scans and risk analysis of the digital footprint of suppliers or partners (aka attack surface scans). Because not all risks can be identified in an automated manner, Ceeyu also offers the possibility to collect certificates and audit reports, and to carry out digital questionnaire-based audits. The latter can be done by creating questionnaires tailored to the supplier, from a white sheet or starting from templates that Ceeyu makes available. The completion of the questionnaire by the supplier and the follow-up of the process by the customer is done in a secure environment on the same SaaS platform. The platform enables a simple, central follow-up of supply chain risks, entirely online and without the intervention of third parties. The closed platform guarantees the confidentiality of the assessments and data, since only authorized persons have access to the application.
At Netsmart we combine the agility of cutting-edge technologies with our extensive experience to deliver effective cybersecurity solutions. We partner with businesses to develop and implement advanced security solutions, continuously monitor evolving threats, and ensure a swift and effective response to cyber incidents. With a distinguished team of expert engineers, industry-leading vendors, and 25 years of experience, we offer an integrated approach covering networks, infrastructures, data, and cybersecurity, safeguarding your digital infrastructure.
At ONE Conference we chose to address a rising concern of our customers. Do you know 76% of organizations have had an API-related breach in the past year?
APIs serve as leading attack vectors due to the sensitive data they handle and their role as data gateways for companies and organizations. Traditional network and web protection tools are insufficient in fully securing APIs from all threats, including those listed in the OWASP API Security Top 10. Inadequate detection and response mechanisms can lead to challenges in identifying and remedying API attacks.
With Netsmart expertise and Akamai Api Security solution, we provide a complete API Security Platform that locates and inventories all dormant, legacy, and zombie APIs regardless of configuration or type. Furthermore, with the application of machine learning technology, we can effectively detect anomalies in API usage behaviours.
Key features are: Gain 100% visibility from all data sources across on-prem and cloud /Automatically discover APIs, domains, and issues /Build a robust API inventory and easily find exploitable intelligence /Discover sensitive data in the API channel /Identify vulnerabilities on APIs in the development lifecycle with CI/CD pipeline integrations/ Identify business-logic-based attacks immediately/Reduce Mean-Time-To-Resolution (MTTR)/Fully align with security operations centre (SOC)processes.
By 2025, over 50% of data theft will be due to unsecure APIs. We can help you comply with the NIS2 Directive by ensuring the security of your APIs. Join us at our booth!
We believe that all businesses should be empowered to protect themselves against several forms of cybercrime. That’s why we created the intelligent platform ReConfirm. ReConfirm allows companies to fully control their External Attack Surface by investigating, identifying, and neutralizing critical cybersecurity risks they weren’t even aware of.
The External Attack Surface of an organization consists of all assets that are accessible or discoverable via the internet. This includes computers, servers, websites, email systems, as well as leaked employee accounts and passwords. Hackers can easily gain insight into this external attack surface and get a clear picture of the vulnerabilities and risks present within it.
With their risks no longer hidden, companies operate more confidently, securely, and effectively.
ReConfirm is a Dutch cybersecurity company. Started by two experts with 20+ years of combined experience in offensive and defensive cybersecurity, ReConfirm focuses on daily technological innovation. ReConfirm collaborates with ESET NL on development and sales, combining market knowledge to deliver a high-end solution. Secure-by-nature is the ethos of ReConfirm, which earned it the label “Cybersecurity Made in Europe.” This demonstrates ReConfirm’s adherence to European cybersecurity standards, including secure software development and data protection.
Visit the booth of dcypher and NEXIS to learn more about national and European funding opportunities, to find collaboration partners and expertise to turn research into effective applications and the cybersecurity program within the Human Capital Agenda for ICT.
dcypher, is the collaboration platform for cybersecurity research and innovation in the Netherlands, connecting organisations, knowledge institutes and government bodies.
NEXIS, the National Coordination Centre for Cybersecurity Innovation (NCC-NL), aims to promote knowledge exchange, cooperation and innovation in cybersecurity between the Netherlands and Europe.
Quantum Gateway Foundation is a cybersecurity solution provider that helps companies and governmental organisations to prepare for a Quantum-Safe future and to become resillience against the Quantum threat, caused by the future capability of Quantum computers to break most of the encryption protocols that are being used for communication and ecnryption of sensitive data world wide.
The goal of Quantum Gateway Foundation is to assist people on this difficult journey with cryptography discovery, quantum-safe design and post-quantum protection solutions and services. Three current offerings of Quantum Gateway Foundation are:
1) Quantum Shield, a cryptography discovery tool that provides security leaders and specialists with statistical insight of their current (post-quantum) cryptography resilience environment, upgrading your cryptography management from ad-hoc to understood, measured and in-control.
2) The Quantum-Safe testbed helps organisations to experiment with, simulate and compare different cryptography protocols and provides essential inputs to develop the optimal strategy for their cryptography migration projects.
3) Quantum Path (patent pending) is a secure communication tunnelling solution that creates instant quantum-safe channels without requiring changes or interruptions to existing end-user or business applications.
If you need more information, please visit us at the One-Conference Expo and quantumgateway.foundation
Our vision is a world where each day is safer and more secure than the one before. Our Mission is to be the cybersecurity partner of choice, protecting our digital way of life.
Palo Alto Networks, the global cybersecurity leader, continually delivers innovation to enable secure digital transformation even as the pace of change is accelerating.
We enable cyber transformation via our best-of-breed platforms; Network Security, Code to Cloud and Autonomous SecOps. Our world-class threat intelligence and advisory experts deliver what’s next in cybersecurity.
Prepare for and eradicate threats in partnership with world-renowned threat researchers, incident responders and security consultants. Collaboration is of most importance in cyber security and in the case of Quantum Encryption we collaborate with Quantropi. Quantropi provides data security powered by quantum mechanics. Today’s encryption and cryptographic keys will be no match for the Y2Q Quantum Threat. Feel free to visit our booth to learn more.
At Roseman Labs we have built a groundbreaking solution to train and use AI on data that is too sensitive to be shared. Our solution is used by 150+ organizations across Healthcare, the Public Sector and Financial Services to solve real world problems.
The Roseman Labs platform enables you to encrypt, link and analyze multiple data sets, while safeguarding the privacy and commercial sensitivity of the underlying data. You can combine information from several organizations, run your analyses on the aggregated records at a granular level, and generate new insights – all without ever being able to view other participants’ input. You get the insights you need, while the data stays protected.
Our software employs a cryptographic technology called Multi Party Computation that encrypts all data from beginning to end. This means enables data owners always to stay in control of how their data is processed, enhancing privacy compliance through data minimization and proportionality.
Through the ease of a familiar Python interface, you can enjoy 50+ ready to use functionalities, ranging from basic operations to machine learning and regular expressions. These features unlock previously inaccessible information without compromising data privacy, offering more detail into statistics including time efficiency, product effectiveness, cost savings, resource allocation, and risk analysis.
NCSC’s SecureNed data collaboration platform is powered by Roseman Labs technology.
Ismijnbedrijfveilig is a knowledge platform initiated by its parent company, Vallem. Vallem is a cybersecurity firm specializing in protecting small and medium-sized businesses (SMBs). The initiative was born out of Vallem’s daily interactions with entrepreneurs who, due to their own lack of knowledge, face significant risks. Recognizing this critical need, Ismijnbedrijfveilig was created to bridge the knowledge gap.
Ismijnbedrijfveilig provides SMB owners with direct insights into their digital security through a comprehensive questionnaire. Based on the results, we offer tailored knowledge and tools to help entrepreneurs take the first steps towards a digitally secure business.
Additionally, Ismijnbedrijfveilig offers information on all relevant topics for SMBs, ensuring that all their questions are answered on this platform. Our aim is to bridge the knowledge gap between SMBs and cybersecurity through this social initiative. This initiative is completely free and truly designed to help Dutch entrepreneurs. All knowledge, tools, and ready-to-use policies are offered at no cost to keep the barrier as low as possible.
At Nautilus Cyber Security, we specialize in protecting your OT and IoT infrastructure from the alarming rise in OT cyber threats. Given the high impact of OT cybersecurity breaches, it is crucial to ensure the security of all your assets. Our platform offers proactive asset discovery, robust vulnerability management, and real-time monitoring across various OT protocols. This comprehensive approach empowers you to effectively mitigate risks.
Additionally, we provide an advanced AI-based reporting engine tailored for C-Level executives, enabling a thorough assessment of the company’s cybersecurity risk posture. As an EU-based provider, our data and services comply with EU regulations and standards, including the NIS2 Directive, ensuring that data sovereignty is maintained within the EU.
At Nautilus OT, our mission goes beyond protection; we empower businesses with the necessary tools and insights to secure their future in an increasingly connected world.
FlashgroupXR, in collaboration with KPMG, presents an innovative cybersecurity scenario training in Virtual Reality (VR).
This training aims to enhance how organizations prepare for and respond to cyber threats through immersive and realistic simulations.
Our VR-based training focuses on a ransomware attack scenario targeting crane operation systems at a large container terminal. Participants will be placed in a high-pressure environment where they must react to the crisis, learning to identify, mitigate, and manage cyber risks effectively. The training environment includes a detailed simulation of a container terminal and a board room, providing a comprehensive experience of the incident’s impact.
The training aims to improve participants’ ability to recognize incidents, execute their roles effectively, and understand the roles of key stakeholders. Participants will also learn to cope with high-stress situations and make complex decisions. The VR scenarios are designed to evolve based on participants’ decisions, providing a dynamic and engaging learning experience.
At the ONE Conference, we invite you to explore how our collaboration sets new standards in cybersecurity training. Experience firsthand how VR can transform your organization’s approach to cybersecurity, making it more engaging, effective, and impactful.
Visit our booth to learn more about FlashgroupXR, KPMG, and our groundbreaking VR cybersecurity scenario training.
Clember is an AI-powered cybersecurity platform that makes elite-level security guidance affordable and always available. With Clember, you get immediate CISO-level insights and easy-to-follow, step-by-step guidance to enhance your cybersecurity from day one.
Many customers choose Clember for its instant and continuous results, avoiding the long wait times and high costs of traditional assessments. Clember’s unique combination of AI, human expertise, digital feeds, and continuous scanning provides real-time understanding and contextual insights into your organization’s threats and improvements.
Our approach ensures you start with the right actions and continuously improve your security. We believe no company should be vulnerable just because they can’t afford it.
Experience the confidence of elite-level cybersecurity with Clember. Don’t wait—act now.
RiskStudio provides an intuitive intelligence platform, acting as a virtual CISO, designed to
help organizations enhance their cyber resilience and maintain compliance seamlessly.
Our solution is tailored for medium-sized businesses that may lack extensive resources and
authority but face emerging cyber threats, European directives like NIS2, and new annual
reporting requirements.
RiskStudio delivers value by enabling:
• Board Members: To make informed strategic decisions.
• Security Officers: To meet the demands of internal and external stakeholders.
• Managers: To engage their teams with relevant risk information.
• Employees: To contribute to the company’s security efforts.
• Security Teams: To address incidents efficiently and communicate risks effectively.
By leveraging automated information gathering, risk profiling, and AI-supported analysis of
millions of pre-processed observations, RiskStudio helps organizations reduce risk
assessment cycles from months to days, all while minimizing the need for extensive
employee involvement.
Key features of RiskStudio, which will be showcased at the expo, include:
• Daily Updated Security Ratings: For supply chain companies.
• Comprehensive Risk Templates: Covering the most common laws, regulations,
standards, and security frameworks, enabling a quick start.
• Employee Engagement Tools: Providing instant feedback on reported events.
• Automated Risk Profiling and Prioritization: To streamline risk management.
• Organization Maturity Monitoring and Guidance: For continuous improvement.
• GAP Analysis and Program Advice: Using natural language processing.
Cloudflare, Inc. (NYSE: NET) is the leading connectivity cloud company. It empowers organizations to make their employees, applications and networks faster and more secure everywhere, while reducing complexity and cost. Cloudflare’s connectivity cloud delivers the most full-featured, unified platform of cloud-native products and developer tools, so any organization can gain the control they need to work, develop, and accelerate their business.
Powered by one of the world’s largest and most interconnected networks, Cloudflare blocks billions of threats online for its customers every day. It is trusted by millions of organizations – from the largest brands to entrepreneurs and small businesses to nonprofits, humanitarian groups, and governments across the globe.
Hack the Boat